
In today’s hyper-connected digital landscape, where our lives are increasingly intertwined with mobile devices, the threat of cyberattacks has evolved to become more cunning and deceptive than ever before. Among the arsenal of digital trickery that cyber criminals employ, one deceptive tactic stands out: smishing.
Statistics last year show that during the first six months of 2021, smishing reports grew by 700%, compared to the second half of 2020.
The fact is, no matter the size of the name or brand, nobody is safe, as was highlighted by the attack that Royal Mail endured in March 2021, resulting in millions of people being scammed in one single, yet simple, hit.
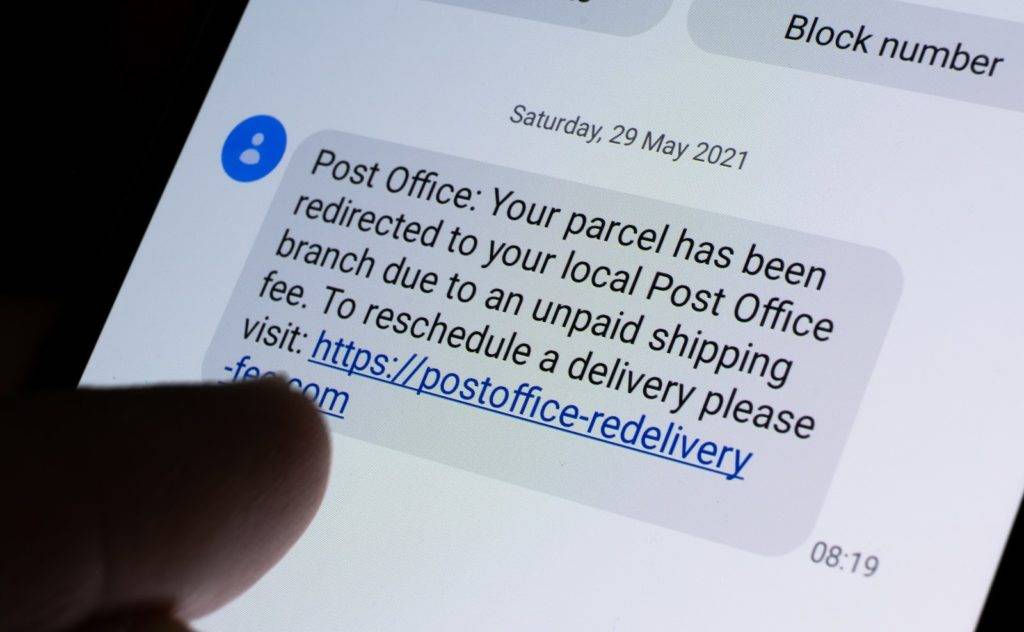
But what is smishing, and how can you protect yourself from falling prey to these insidious ploys? This comprehensive guide will equip you with the knowledge and tools to navigate the dangerous waters of smishing with confidence and security.
In this guide to smishing, we will go through:
- What smishing is
- The difference between smishing and phishing
- Different types of smishing attacks
- How smishing attacks work
- Real-world examples of smishing attacks
- What you should do if you fall victim to a smishing attack
- How to protect yourself from smishing
- FAQs
- Final thoughts
What is smishing?
Smishing is a deceptive and malicious cyber tactic that cybercriminals employ to target individuals via SMS messages. At its core, smishing is a form of phishing attack that leverages the immediacy and familiarity of SMS to deceive and manipulate recipients.
Imagine this scenario: you receive an unsolicited text message on your smartphone, claiming you’ve won a tempting prize or warning of an urgent security breach. It’s a message that demands immediate attention, tugs at your curiosity, or sparks a sense of urgency. These are the hallmarks of a smishing attack.
The difference between smishing and phishing
Phishing and smishing are both forms of cyberattacks that aim to deceive individuals into revealing sensitive information or taking harmful actions. The primary difference between them lies in the communication channel used:
Phishing:
- Phishing is typically conducted via email, but it can also occur through other communication methods like social media, instant messaging, or even phone calls.
- In phishing attacks, attackers send fraudulent messages that appear to come from legitimate sources, such as banks, government agencies, or well-known companies. These messages often contain links to fake websites that mimic the appearance of the real ones.
- The goal of phishing is to trick recipients into providing sensitive information, such as login credentials, credit card numbers, or personal identification details, on the fake websites.
Smishing:
- Smishing is a specific type of phishing attack that occurs through SMS (text) messages sent to mobile phones.
- Similar to phishing emails, smishing messages often impersonate trusted entities or services and include links to fake websites.
- The primary difference is that smishing attacks use text messages as the delivery method instead of email.
In both phishing and smishing attacks, the ultimate goal is to steal personal information or credentials, distribute malware, or trick individuals into making financial transactions.
To protect yourself from these types of attacks, it’s important to be cautious when receiving unsolicited messages, not click on suspicious links, verify the authenticity of the sender or organisation, and never provide sensitive information without confirming the legitimacy of the request through official channels.
Different types of smishing attacks
When it comes to smishing, cybercriminals employ a range of tactics to deceive and manipulate their targets. To protect yourself effectively, it’s essential to understand the diverse landscape of smishing attacks. Below, we’ll explore several common types of smishing that you should be aware of:
1. Prize or gift smishing
In this type of smishing, scammers send text messages claiming that you’ve won a prize, gift card, or valuable item. They may ask for personal information or direct you to a fraudulent website to claim your “winnings.” Be cautious of messages that promise something for nothing.
2. Security alert smishing
Scammers often impersonate banks, payment providers, or online services, sending fake security alerts via text messages. They might claim unauthorised access to your account, urging you to click on a link to verify your identity. These messages aim to steal your login credentials.
3. Fake charity smishing
Cybercriminals may exploit your goodwill by sending smishing messages that appear to be from charitable organisations. They request donations or support for a supposed cause. Verify the legitimacy of such requests before making any contributions.
4. Delivery or package smishing
With the rise of online shopping, smishers send messages posing as delivery services or couriers, claiming issues with your recent order or delivery. They may request payment or personal details to resolve the supposed problem.
5. Government agency smishing
Scammers impersonate government agencies, such as the HMRC or immigration services, to create a sense of urgency. They claim issues with your documentation, taxes, or immigration status, pressuring you to take immediate action.
6. Social engineering smishing
This type of smishing involves emotional manipulation. Scammers send messages that tug at your heartstrings, such as a distressing story or a plea for help from a friend or family member. Their aim is to exploit your empathy to extract money or information.
7. Malware-loaded smishing
In some cases, smishing messages contain links to download malicious software onto your device. Once installed, this malware can compromise your security and privacy, potentially leading to identity theft or unauthorised access.
8. App download smishing
Cybercriminals may pose as legitimate companies or app stores, encouraging you to download a particular app or click on a link to update an app. These messages can lead to the installation of malicious software or the compromise of your app accounts.
How smishing attacks work
To defend against smishing effectively, you need to grasp how this deceptive tactic operates. In this section, we’ll break down the mechanics of smishing, revealing the strategies cybercriminals use to manipulate and deceive their targets.

By understanding these tactics, you’ll be better equipped to recognise and protect yourself from smishing attacks.
1. Initial contact
You receive an unsolicited text message on your mobile device. This message is designed to grab your attention and often carries a sense of urgency or importance.
2. Deceptive content
The content of the message may vary depending on the type of smishing attack. It could claim that you’ve won a prize, alert you to a security breach, or inform you of suspicious activity on your account. Some messages may even pose as charitable requests or distress calls from friends or family members
3. Request for action
The smishing message typically prompts you to take immediate action. This may involve clicking on a link, calling a phone number, or providing personal information. The urgency is a key element of the attack, as it aims to pressure you into complying.
4. Deception techniques
To make the attack more convincing, smishers employ various deception techniques:
- Spoofed sender information – attackers can manipulate the sender’s information to make it appear as though the message is from a trusted source.
- Fake URLs – links in the message may lead to fraudulent websites that mimic legitimate ones, making it challenging to discern the difference.
- Emotional manipulation – some smishing attacks play on emotions, using distressing stories or pleas for help to elicit a response.
5. Data theft or malware
If you follow the instructions in the message, you may unknowingly share sensitive information, such as login credentials, credit card details, or Social Security numbers. In some cases, clicking on links can lead to the download of malware onto your device, compromising your security.
6. Objective achieved
Once you’ve taken the desired action, the attacker achieves their objective, which could include stealing your personal or financial information, gaining unauthorised access to your accounts, or delivering malware for future exploitation.
Real-world examples of smishing attacks
Here are a few real-world examples of smishing attacks:
IRS tax scam
In the United States, scammers have sent SMS messages claiming to be from the Internal Revenue Service (IRS). These messages typically inform recipients that they owe back taxes or that there is a problem with their tax return.
The messages contain a link or phone number to resolve the issue. Victims who follow the link or call the number are directed to a fake IRS website or automated phone system where they are asked to provide personal and financial information, which is then used for identity theft or fraud.
COVID-19 vaccine appointment scams
During the COVID-19 pandemic, scammers took advantage of the vaccination rollout by sending smishing messages offering fake vaccine appointments or claiming to represent government health agencies.
These messages requested personal information, payment for appointments, or directed recipients to malicious websites posing as vaccine registration sites.
Package delivery scams
Scammers have sent SMS messages impersonating well-known e-commerce and delivery companies, such as Amazon and FedEx. These messages often claim that a package delivery has been delayed or requires additional information.
Recipients are then prompted to click on a link or provide personal details to resolve the issue, but in reality, this information is harvested by the attackers.
Bank account verification scams
Some smishing attacks involve fraudulent messages appearing to be from a recipient’s bank.
These messages may claim that the recipient’s account has been compromised and ask them to verify their identity by clicking on a link or providing sensitive account information. Victims who fall for this scam risk having their bank accounts drained by attackers.
These are just a few examples of real-world smishing attacks that have occurred. Smishers continuously adapt their tactics and may impersonate various organisations to deceive individuals.
It’s essential for people to remain vigilant and cautious when receiving unsolicited text messages, especially those that request personal or financial information. Legitimate organisations typically don’t request sensitive information through SMS, and it’s advisable to independently verify the information with the organisation using official contact details rather than relying on the text message.
What should you do if you encounter a smishing attack?
Encountering a smishing attack can be unsettling, but it’s essential to stay calm and take swift action to protect yourself.

Here’s your action plan for responding effectively to a smishing attack:
1. Don’t respond or click
When you receive a suspicious text message, resist the urge to respond, click on any links, or call any phone numbers provided in the message. Engaging with the attacker can further compromise your security.
2. Verify the source
If the message claims to be from a legitimate organisation, independently verify its authenticity. Use official contact information from the organisation’s website or other trusted sources, not the contact details provided in the message.
3. Don’t share personal information
Under no circumstances should you share personal information, such as your national insurance, passport or NHS numbers, credit card details, or login credentials, in response to a text message.
4. Delete the message
Delete the suspicious text message from your device, which reduces the risk of accidentally engaging with the attacker’s content.
5. Report the attack
Report the smishing attack to your mobile service provider as they may have specific channels or instructions for reporting such incidents.
6. Warn contacts
If you received a smishing message from a contact’s compromised account, inform them about the incident. Their account may have been hacked, and they should take action to secure it.
7. Change passwords
If you suspect your account credentials have been compromised, change your passwords immediately. Use strong, unique passwords for each account and consider using a password manager to keep them secure.
How to protect yourself from smishing
Protecting yourself from smishing attacks involves being vigilant and taking certain precautions to minimise the risk of falling victim to such scams. Here are some steps you can take to protect yourself from smishing:
- Exercise caution – be vigilant when receiving unsolicited text messages, especially from unknown senders. Approach them with scepticism and a critical eye.
- Question urgency – smishing messages often create a sense of urgency. Take a moment to consider whether the urgency is legitimate or a tactic to manipulate you.
- Educate yourself and others – stay informed about the latest smishing tactics and scams as knowledge is your first line of defence. Be aware of common types of smishing messages and how they operate, share your knowledge about smishing with friends and family and encourage them to remain vigilant and informed as well.
- Install security software – equip your mobile device with reputable antivirus and anti-malware cybersecurity software as these tools can help detect and block smishing attempts.
- Enable spam filters – most smartphones have built-in spam filters for text messages, which when enabled can automatically flag and filter out suspicious messages.
- Multi-Factor Authentication (MFA) – implement multi-factor authentication (MFA) on your accounts whenever possible as this adds an extra layer of security by requiring multiple forms of verification.
- Use strong and unique passwords – avoid using easily guessable information such as birth dates or common words and consider using a password manager to keep track of your passwords securely.
- Check for secure websites – when prompted to enter personal information online, ensure the website’s URL begins with “https://” and look for a padlock icon in the address bar.
- Regularly update software – keep your devices’ operating systems and apps up to date as these updates often include security patches that protect against known vulnerabilities.
- Report suspected attacks – if you encounter a smishing attempt, report it to your mobile service provider and relevant authorities, such as the National Cyber Security Centre (NCSC) as this helps identify and take action against attackers.
- Trust your instincts – if something feels off about a text message, trust your instincts. It’s better to be cautious than to fall victim to a smishing attack.
FAQs
How can I differentiate between a legitimate text message and a smishing attempt?
Legitimate messages often come from known contacts or official sources. Smishing text messages may use urgent language, generic greetings, or suspicious sender information. Always verify the source and be cautious of unsolicited messages.
What should I do if I’ve already clicked on a suspicious link in a smishing message?
If you’ve clicked on a suspicious link, immediately disconnect from the internet, run a security scan on your device, change passwords for your accounts, and monitor your accounts for unusual activity. Consider contacting your bank or service provider if necessary.
Are there any mobile apps that can help protect against smishing attacks?
Yes, there are mobile security apps available that offer protection against smishing and other threats. Look for reputable antivirus and anti-malware apps in your device’s app store and keep them up to date.
What should I do if I receive a smishing message from a known contact?
If you receive a suspicious message from a known contact, it’s possible their account has been compromised. Contact the person through another method (e.g., phone call or alternative messaging app) to confirm the message’s authenticity and inform them of the situation.
How do smishers obtain my phone number in the first place?
Smishing attackers often acquire phone numbers through various means, including:
- Data breaches – stolen data from previous breaches may include phone numbers.
- Online forms – providing your phone number on websites or social media can expose it to data collectors.
- Public records – phone directories, social media profiles, and public records can be sources of phone numbers for attackers.
Final thoughts
Smishing may be devious, but it is not insurmountable. Armed with the insights you’ve gained in this guide, you possess the tools to navigate the digital world with greater confidence, security, and peace of mind.
If you have a way that you can be contacted, then you’re at risk. It’s as simple as that. Without taking yourself off-grid, there is no way of taking yourself out of the loop and being targeted.
While SMS is growing, we can’t discount email. We live in a world where scammers and criminals are using several different tactics depending on the data they’re trying to get, a blend of both SMS and email in a frighteningly convincing way.
As a user, we’re required to have a multi-layered security approach – one that incorporates up to date education but also investment in software across our digital devices to ensure you, your business, or your staff, don’t fall foul of these tactics.
If you would like to find out more information about our network security services or if you have any more questions about smishing, please don’t hesitate to contact us.